
The “JonSnow” challenge under the “Reverse Engineering” category of the ZeroDays Capture the Flag 2018 event was pretty interesting as it took me some time to realize what was obvious. So to start with, the challenge description went as follows:

You know the flag?
Tell me what you know Jon Snow?
The first thing to see was what the file was by using the command “file”:
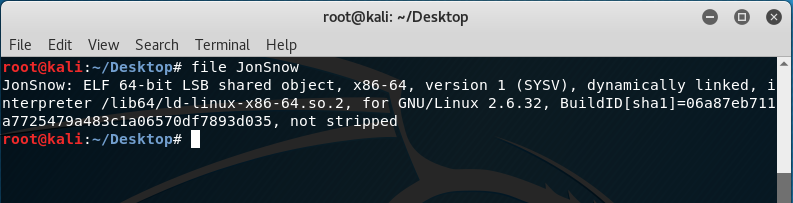
When I saw that this was a 64-bit ELF, I knew that I won’t be able to play around because I was using a 32-bit Kali during the event! Talk about not being prepared. So, here I am, not being able to sleep soundly just like my OSCP days because an unsolved challenge gave me nightmares. The only thing that I was able to do apart from the “file” command was using “strings” but it honestly did not make sense:
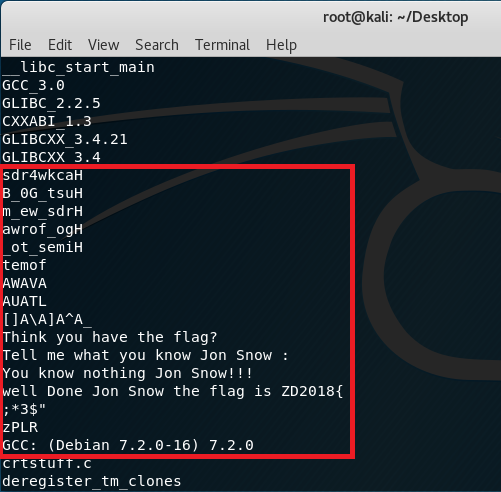
When I was able to install a 64-bit Kali, the excitement went up. The first command was:
gdb ./JonSnow
After loading the ELF file into the debugger, doing a “disas main” should pretty much show the assembly instructions found in the main function:

The concern here starts at <+9> because the previous lines are just some memory adjustment instructions.
0x0000555555554c93 <+9>: movabs $0x61636b7734726473,%rax
0x0000555555554c9d <+19>: movabs $0x7573745f47305f42,%rdx
0x0000555555554ca7 <+29>: mov %rax,-0x50(%rbp)
0x0000555555554cab <+33>: mov %rdx,-0x48(%rbp)
Notice that literal values are being passed into the RAX and RDX register so they can be transferred into the stack. The index where this all starts is at -0x50(%rbp) as seen at <+29> and this seems to continue up to -0x24(%rbp) at <+86> as a “word” because of movw (If it was, movb, then it should be a single byte) so the goal here would be adding a break point after all these literal to memory movements and then dump the stack contents.
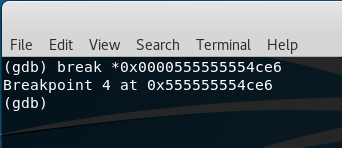
To add a break point at <+92>, type in the following command (Please note that you might have a different address):
break *0x0000555555554ce6
Now that we have a break point, we can now proceed to debug the program.
To debug the program, type in the “run” command.
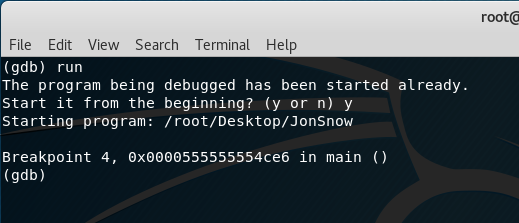
The program pauses its execution because of the break point. At this time, we should try dumping the stack contents starting from the index -0x50(%rbp) as stated previously using the command:
print (char*)($rbp-0x50)
Interestingly, the flag can be read backwards. “Sometimes_to_go_forwards_we_must_G0_Backw4rds”.

To confirm this, we run the executable file normally through the terminal and test the key:
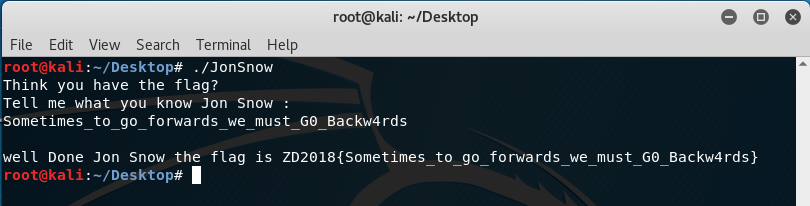
Finally, the flag is: ZD2018{Sometimes_to_go_forwards_we_must_G0_Backw4rds}
