ZeroDays CTF 2018 – “Whatta Man” Challenge
The "Whatta Man" challenge under the "Reverse Engineering" category of the ZeroDays Capture the Flag 2018 event got me quite confused probably because I got intimidated by those system calls presented in the debugger. So to start with, the challenge description went as follows:
OK ladies lets hear it for Khal Drogo
First was the need to check what the file was:
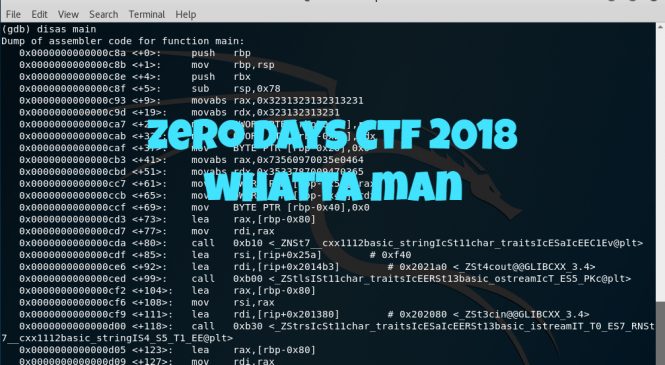
Another 64-bit ELF here which means the debugger has to be 64-bit too! Apart from doing the initial investigation on the file format, doing the "strings" command to extract strings in the executable gave an output of:
Looking at the above picture doesn't give us any flag so the next step would be running the program to get an idea of how it works before using a debugger to do some assembly language review:
...