ZeroDays CTF 2018 – “Hodor” Challenge
Another reverse engineering challenge from the ZeroDays Capture the Flag 2018 event was named "Hodor". The challenge description went as follows:
Oh you said Hodor!
I thought you said Harder!
The first thing to do is check what the file is:
The file is a 64-bit ELF which means we need to have a 64-bit support for the debugger. Before anything else however, doing "strings" shows the following output:
Since the output doesn't really show anything interesting for the flag, running the executable should output:
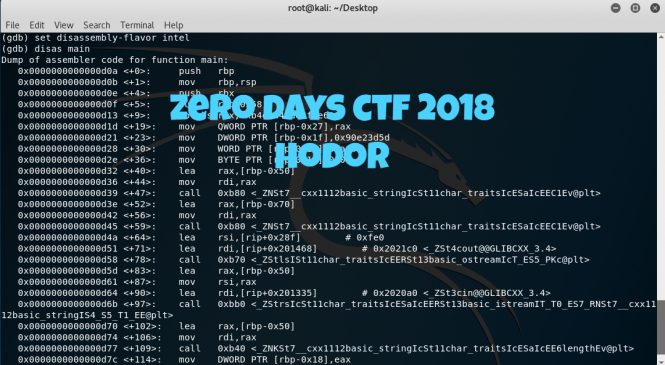
Similar to the challenge "WhattaMan", it is asking for a flag input to check if it's correct or not. By entering the command "gdb ./Hodor", GDB should load the executable for debugging:
Again, similar to the challenge "WhattaMan", doing "info...