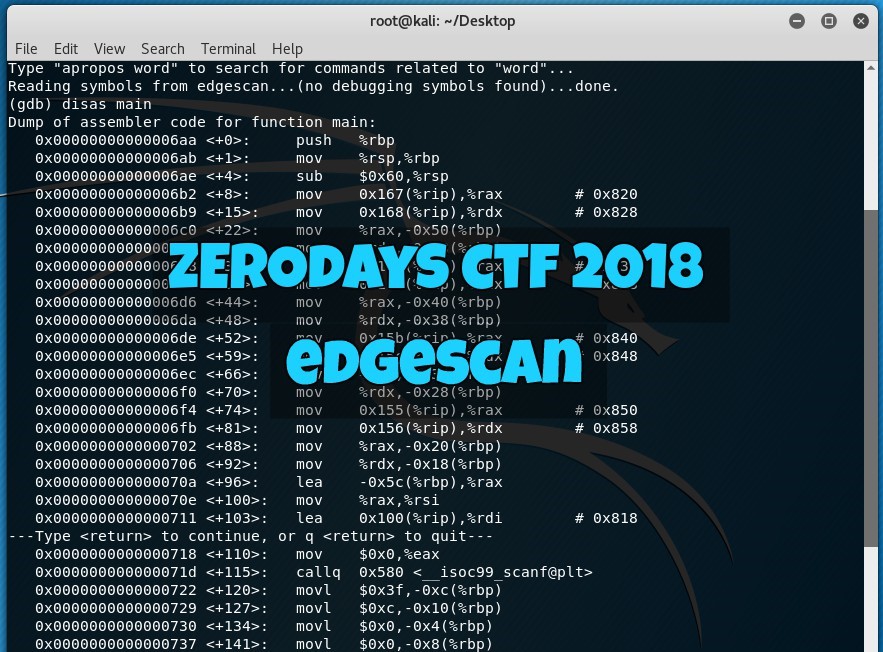
The “edgescan” challenge under the “Reverse Engineering” category of the ZeroDays Capture the Flag 2018 event was pretty straightforward although I wasn’t able to solve it during the actual event due to time pressure. So to start with, the challenge description went as follows:
So edgescan kindly sent us a small challenge, we’ve tweaked it slightly.
Enter the key to get your flag.
Enjoy!
Clues:
The flag is in the usual format.
The flag message is XORed with the key (12 chars).
The first clue says “The flag is in the usual format” which means, it should be in the format of ZD2018{???????????????????} as per example flags given in the event. The second clue on the other hand says that the flag message is XORed with a 12-character key. During the event, I actually thought that the key was hiding inside the executable file provide so I fired up gdb and tried disassembling it.

This is where I got stuck because I had to review my assembly language and gdb powers! (It has been quite a while). So yeah, I went down a rabbit hole with this. A few days after the event, I just had the most embarrassing realization of the year.
Going back to the clues, the solution was pretty simple. Just enter the ‘known’ parts of the flag as the key and it will throw the real one as the output! This is basically just taking advantage of the XOR operation. Since the flag is in the ZD2018{???????????????????} format, this means that the first 7 characters “ZD2018{” will enable us to get the partial key. Typing the following will reveal the first 7 characters of the key:
./edgescan <<< ‘ZD2018{AAAAA’
Note that I have added 5 upper case letter ‘A’s to have a 12-character key as the input. The output reveals the first 7 characters of the key which is “Sponsor”.
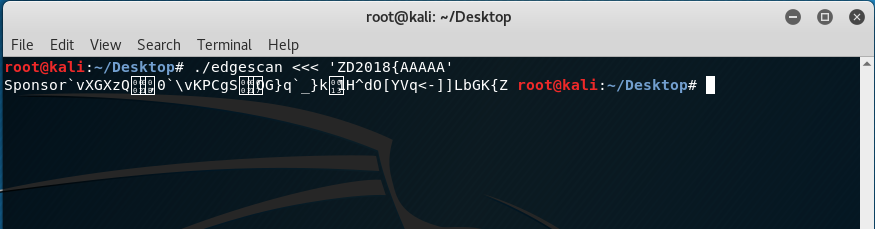
To continue, “Sponsor” was now used instead of the partial flag “ZD2018{” which shows the following result:
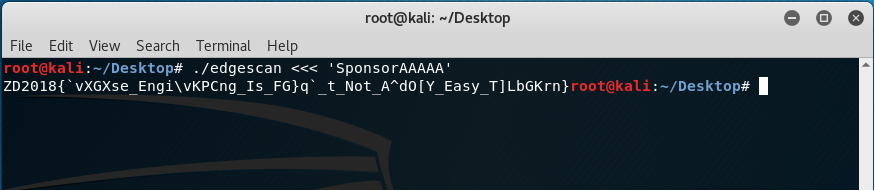
Just by guessing, the first word could probably be “reverse” because of the “Engi” after the underscore but since the letter “E” from the word “Engi” (which is probably “Engineering”) is in uppercase, then we try replacing the first “A” from the key with letter “R”.
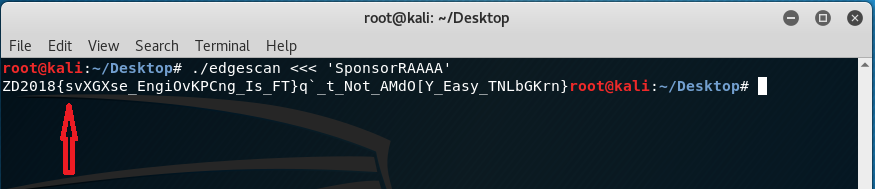
The output shows a letter “s” which means this becomes the next character of the key so to confirm, we now replace “R” from the key into “s” and we’ll get the following:
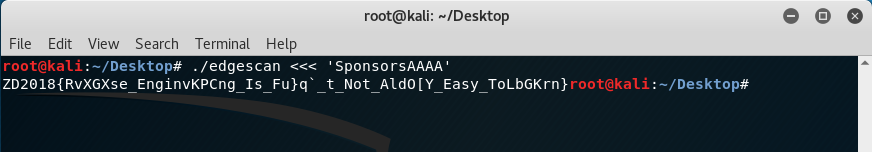
Doing the previous steps until character “A’s” got replaced presented the following:
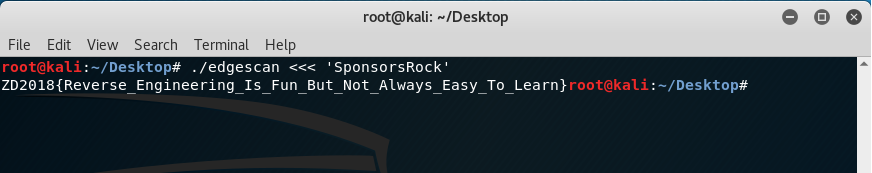
The key to decrypt was “SponsorsRock” while the flag for the challenge was ZD2018{Reverse_Engineering_Is_Fun_But_Not_Always_Easy_To_Learn}
